Backdoors in practical QKD
Since it was originally proposed in 1984, a lot of effort has gone into proving the security of quantum key distribution. These theoretical proofs have evolved from highly idealized scenarios to incorporating some imperfections, but ultimately are based on a set of assumptions.
We explore deviations from these assumptions which lead to the cryptographic systems becoming insecure. In particular, we look at timing information that is publicly exchanged by the communicating parties. All single photon implementations of QKD identify a photon from backgroun by measurement of the arrival time at detectors. In principle, there should be no correlations between this arrival time and the result of the measurement.
Measurement setup
 |
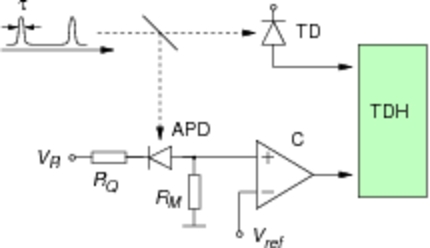 |
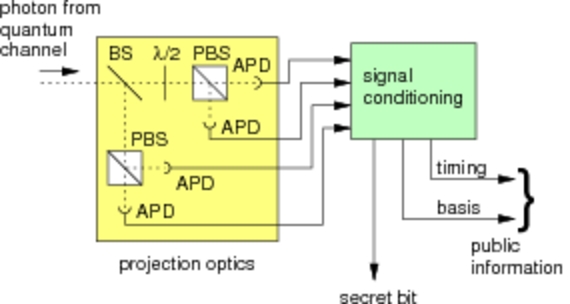
| Figure 1. Configuration of photocounting detector and polarization analysis for QKD with a passive basis choice. | Figure 2. Experimental setup to characterize the timing jitter of a single photodetector. A train of ultrashort light pulses from a mode-locked Ti:Sa laser are sent into the 4 detector module and the response time of the detectors is characterized. |
Detector response and information leakage
The detector response is non-identical for the different APDs representing different measurement outcomes. Since this information is discussed publicly, we must quantify how much information about the key is in principle leaking out to an eavesdropper.
 |
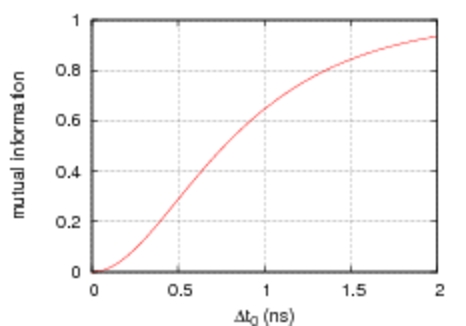 |
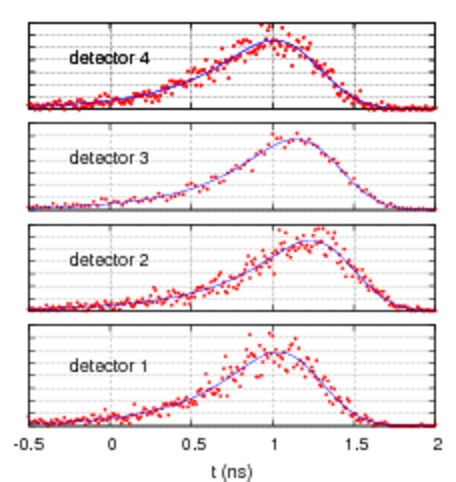
| Figure 3. Photoevent timing histograms for the four detectors in a QKD receiver. The overall shape is similar but the position of the centroid of the distributions can be significantly different. | Figure 4. Eve's information as a function of the delay between detector timing distributions with identical shapes. |
Even relatively small differences in detector response lead to large portions of the key becoming insecure. For example, if the detector response time is equalized only up to half a nanosecond, which is about the intrisic jitter, then Eve could have access to more than 25% of the "secret key".
References
| [1] | A. Lamas-Linares and C.Kurtsiefer: Breaking a quantum key distribution system through a timing side channel. Opt. Express 15, 9388 (2007) |